Environment domains and endpoints
Jahia is designed to handle hundreds of websites per instance which means that many domain names are resolved by the same Jahia environment.
Jahia Cloud offers many features aimed at making the DNS management experience easier:
- Traffic forwarding to Jahia sites based on the public domain being used
- Live traffic swap between two instances when performing upgrades or maintenance
- SSL termination and certificate management
- Domain rewriting with URL rewrite rules
Jahia Cloud endpoints
Public access through the main domain name
Many domains can be configured to target the same Jahia environment. The first step is to configure one or more domain names to point to the relevant Jahia Cloud environment. All incoming traffic first goes through the Jahia Cloud shared load balancers before they are routed to the correct environments.
Binding a domain to your environment
You can specify the external domains that are associated with an environment so that all the traffic towards the domain gets redirected to the right environment. Jahia has multi-site capabilities, and hundreds of domains can be bound to the same environment or the same site. This specifies the domain address that users can use to access your site.
To bind an external domain to your environment:
- In the left panel, select an environment.
- In General>Domains>External domains, enter a domain and click Bind domain.
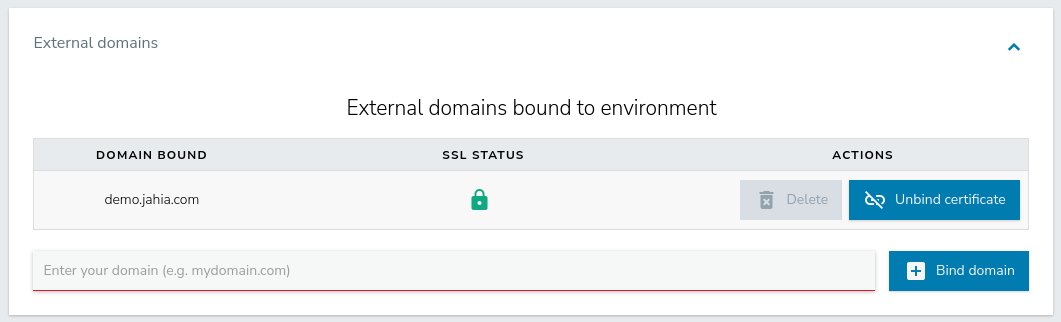
- Click OK in the confirmation message that indicates that binding was successful.
The name of the external domain now displays in the list. You can also click Delete to delete the domain.
Swapping an environment domain
Swap domains when you need to redirect users to another environment. For example, temporarily redirect users to another environment when you upgrade your production environment. The best practice is to backup your production environment before proceeding with an upgrade, and redirect the traffic to the copy before proceeding with the operation.
To swap an environment domain:
- In the left panel, select an environment.
- In General>Domains>Swap bound domains, click Choose your environment and select the environment to redirect to.
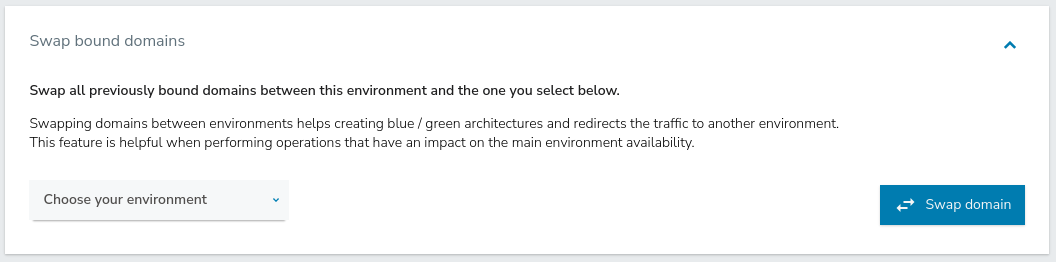
- After selecting an environment, click Swap domain.
- Click OK in the dialog that indicates that the swap was successful.
Note that production environments are monitored in a specific way and are configured to trigger 24/7 alerts to incidence response teams. When switching production traffic, please open a Support so that the right environments are monitored.
DNS configuration
In a typical setup, the DNS configuration of public domain names is the CNAME of a given domain, based on the region where your destination environment is hosted. Those given domains are as follows:
| Region | CNAME |
|---|---|
| AWS US EAST | lb.cloud.jahia.com |
| AWS IRELAND | lb.aws-eu-west-1.j.jahia.com |
| AWS SINGAPORE | lb.apac.cloud.jahia.com |
| OVH FRANCE | lb.ovh.cloud.jahia.com |
If the domain name you need to bind to Jahia Cloud cannot rely on CNAMEs (because it is a root domain or because of DNS provider limitations), create an A-type DNS record with all IPs associated to the relevant region:
| Region | A-type |
|---|---|
| AWS US EAST | 3.233.88.158 18.235.143.165 3.213.234.199 18.213.84.67 |
| AWS IRELAND | 108.129.28.77 52.213.233.197 79.125.85.31 54.73.14.167 |
| AWS SINGAPORE | 47.130.188.199 18.142.78.91 |
| OVH FRANCE |
178.33.40.236 |
Note that these IPs are subject to change and must be updated in your DNS configuration on a regular basis. Jahia Cloud customers receive email notifications to schedule these changes when required.
SSL/TLS certificate management
Add a Certificate
Custom SSL to your custom domain. In Domains, click SSL Certificates and click "Add Certificate".
Wildcard and multi-domain certificates are supported.
To import a certificate into Jahia Cloud, three files are required, and they must all be in PEM format, which is commonly used for storing SSL certificates and their corresponding private keys. Here are the required files and their description
Certificate (.crt or .cer):
- This file holds the certificate itself and includes the signature provided by the Certificate Authority.
Private Key (.key):
- This file contains the private key associated with the certificate.
Intermediate certificate (.csr or .req):
- This file is the Certificate Signing Request and contains essential information, such as the public key and common name, which is necessary for a Certificate Authority to generate and sign a certificate for the requester.
Renew a certificate on the CDN
By submitting a ticket to Jahia Support and providing the necessary information, you can renew a certificate used by our CDN for those who have purchased it.
Bind Certificate
After uploading the certificate, simply select the desired domain from the dropdown menu under 'Actions,' and then click on 'Bind'. For binding several domain names, repeat the domain selection and click 'Bind' for each domain you want to be attached to this certificate.
HTTPS endpoints
The following image shows the typical route used to resolve and route traffic to a Jahia Cloud environment.
.png?t=community750)
- Jahia Cloud shared load balancers
Used to mitigate DDoS attacks and perform an initial HTTPS request validity check. Once checked, the request is routed to the correct Jahia Cloud environment. - Dedicated HAProxy
Lives in the dedicated subnet of the Jahia Cloud organization. HAProxy is primarily used to load balance traffic across all the application servers and to disconnect faulty application servers when detected. HAProxy's configuration is also available to all Jahia Cloud users to upload authentication, security, or URL rewriting rules. - Dedicated Jahia environment
All Jahia Cloud environments are fully dedicated to a single customer and live within the dedicated subnet of an organization.
Public HTTPS access
Public HTTPS access uses the configured public domain pointing to a Jahia Cloud environment, as well as the technical domain provided by default with each environment. No specific configuration is required to enable the public HTTPS endpoint of an environment, but you can configue a basic authentication or a Jahia authentication to filter access.
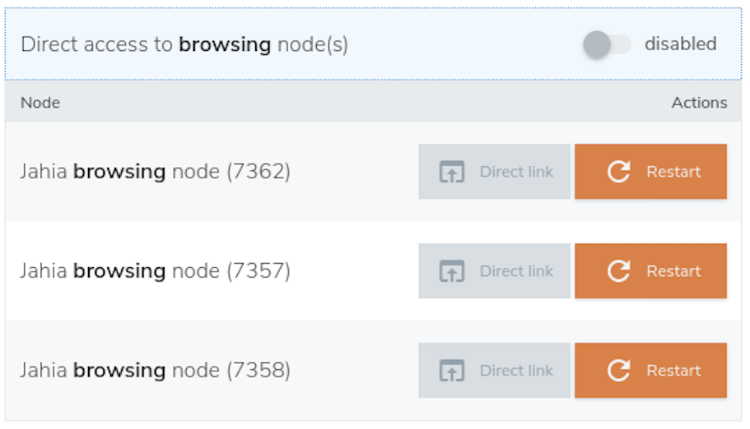
Direct HTTPS access to nodes for troubleshooting purposes
Two methods are offered: direct node access and proxied node access.
.png?t=community750)
Proxied access to a given application server
Proxied access to a given application server (Jahia or jCustomer) goes through the whole network stack (shared load balancer and HAProxy as described in the above graphic) and is subject to HAProxy rules (authentication, security, URL rewriting). It is mainly used for testing or debugging purposes and is ideal for troubleshooting an issue on a specific Jahia or jCustomer node while getting the same experience as public website visitors.
To force a web browser to access a specific application server node, edit the SERVERID cookie of the Jahia or jCustomer website you want to access. The cookie contains a value of the type s<nodeId>. Change the nodeId to the Jahia Cloud nodeId of the application server you need to access directly and save.
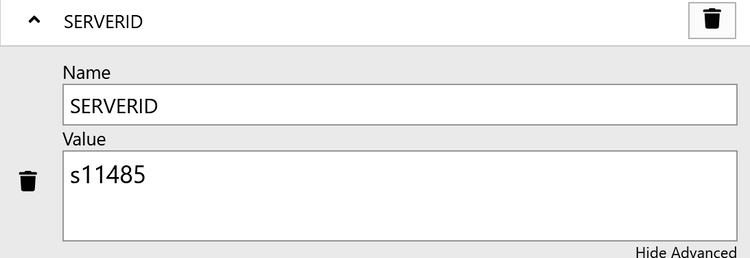
You can find the nodeId of an application server under the Node tab of a given environment.
Direct access to a given application server
Direct access to a given application server can be activated temporarily for troubleshooting purpose only. This feature bypasses HAProxy and all the custom rules deployed in it (authentication, security, URL rewrite rules). However, Jahia authentication remains active and all software-protected resources remain private.