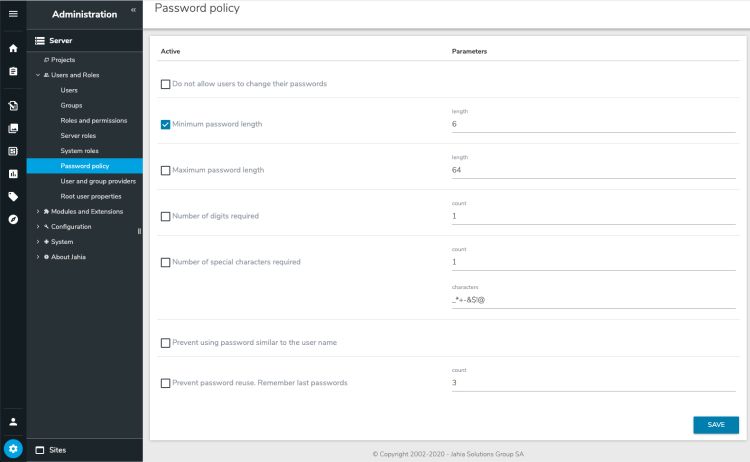
Setting password policies
In the Password policy page, you manage the rules that secure users authentication data. For example, you can set the minimum password length, requirements for special characters, and force users to their change password after a specific period of time.
This section describes how user data is protected and security concerns related to user authentication.
Password encryption
Passwords for Jahia users are stored in the JCR repository one-way encrypted. The default hash algorithm for user passwords is SHA-256 with random 32 byte salt and 4096 iterations. For the root user, Jahia uses a stronger hash: PBKDF2 (Password-Based Key Derivation Function 2) with random 64 byte salt, 32 byte hash size and 8192 iterations.
The password hashing algorithm can be changed for all users and separately for the root user. To change the password hash function, add the following entry into <digital-factory-config>/jahia/jahia.custom.properties , which is by default:
jahia.passwordService.defaultDigester=pwdDigesterSHA256RandomSalt32x4096
This password digester applies to all users in Jahia. You must restart Jahia for changes to take effect. After restarting, all new user passwords (for new users or when passwords are modified for existing users) use the new hash algorithm. Existing passwords continue to work. A password hash is prefixed with an ID of the hashing algorithm, which was used for its encryption.
By default, the following hash algorithms are available in Jahia, in order from weak to very strong:
- pwdDigesterSHA1RandomSalt32x4096
- pwdDigesterSHA256RandomSalt32x4096
- pwdDigesterSHA512RandomSalt32x4096
- pwdDigesterPBKDF2RandomSalt64Key32x8192
Their IDs are self speaking and depict the hashing algorithm used. Note that the stronger the algorithm is, the slower it is in hashing and verifying the passwords (on user login). The default algorithm (pwdDigesterSHA1RandomSalt32x4096) provides a good balance between strength and speed.
Resetting the root user password
Reset the root user by copying a text file with the new password to the data directory. Ensure that your application server has permissions to read the root.pwd file.
To reset the password of the root user:
- Create a plain text file named
root.pwdwith a new root user password in clear text. - Copy the file to the data directory at
<jahia-install-dir>/digital-factory-data. - Restart the server.
You can now login with your new password as root.
Locking a user account
User accounts can be locked either at the global level or site level, depending on the user type. To lock a user account for a:
- global user, see Managing users.
- site user, see Managing site users.
About sensitive user data
Non-public user profile data (user node properties) is not exposed for unauthorized access.
Enabling SSL for logged in users
You can force a switch to an SSL (HTTPS protocol) for a user session, from login to logout. This allows sites with higher security concerns to force secured connections for logged-in users.
To enable SSL for logged-in users:
- Rename the
<jahia-web-app-root>/WEB-INF/etc/config/urlrewrite-ssl.xml.disablefile tourlrewrite-ssl.xml. - In Administration>Server>System>Cache management, click Flush HTML output caches.
- Restart you server.
Now login forms will contain a URL leading to HTTPS and logout links will redirect back to HTTP. This behavior can be adjusted by changing the URL rewrite rules in the urlrewrite-ssl.xml file.